Episode 9 of Mr. Robot’s final season was not only amazing plot-wise but also happily filled with hacks. We discussed [SPOILERS, obvs] IMSI catchers, Raspberry Pis, PGP, phishing telcos and stealing cryptocurrency. (The chat transcript has been edited for brevity, clarity, and chronology.)
This week’s team of experts includes:
- Em Best: a former hacker and current journalist and transparency advocate with a specialty in counterintelligence and national security.
- Trammell Hudson: a security researcher who likes to take things apart.
- Micah Lee: a technologist with a focus on operational security, source protection, privacy and cryptography, as well as Director of Information Security at The Intercept.
- Freddy Martinez: a technologist and public records expert. He serves as a Director for the Chicago-based Lucy Parsons Labs.
- Yael Grauer (moderator): an investigative tech reporter covering online privacy and security, digital freedom, mass surveillance and hacking.
IMSI Catchers
Yael: I thought it was clever of Darlene and Elliot/Mr. Robot to use IMSI catchers.
Micah: I've never had a chance to play with one for real, But they're also referred to as "cell site simulators" because they simulate cell phone towers. Your phone tries to connect to the tower with the strongest signal, so in order to do a man-in-the-middle attack against cell phones, you just need to broadcast a stronger signal than the nearest cell phone tower and nearby phones will connect to your IMSI catcher instead. Then, you forward the traffic to the real cell phone tower, so the phones will still work, but you can spy on/modify all the traffic in the meantime
Yael: I’ve written about them before, but it was about law enforcement use of them for surveillance. They can’t intercept Signal messages, right? So if Deus Group just read a Freedom of the Press Foundation guide, Darlene and Elliot's plot would be foiled.
Em: It will intercept the Signal data, but messages are encrypted until they reach the recipient’s device, so it's not enough to just intercept it.
Micah: Their plot wouldn't have been foiled because Cyprus National Bank still sends two-factor authentication codes (2FA) over unencrypted SMS. I thought it was a nice touch how much Raspberry Pis were represented. In the first scene, in the hotel, the camera panned across some Raspberry Pis, and Darlene was logged in to a Raspberry Pi during the garage door hack.

Freddy: The Raspberry Pi 3 uses USB 3.0, which is fast enough to run a homemade IMSI Catcher.
Em: Homemade antennas are fun. =)
Yael: Oh, did they make their own?
Freddy: You can make your own. I think those are limeSDRs.
Price’s Last Stand
Yael: We had Price in yet another hostage situation.
Em: Yeah, he handled it very well. The traditional ways of getting out of a hostage situation weren't going to work there, but he did several important things for the situation he was in:
1. He kept calm. This is the most important thing. If he had panicked he'd have been killed a lot sooner.
2. He kept Whiterose off balance. His teasing and taunting was beautiful to watch, especially the "wind in his hair" bit.
3. He didn’t give up any important info to accomplish number 2.
4. He provoked Whiterose when they were both visible outside. Walking away after saying what he said almost guaranteed not only that he'd be shot there but that Whiterose would do it—in public.
Yael: My favorite taunts were, “it’s bad management when your best employees either walk off the job or blow their brains out,” and “all this over a little pipsqueak in a hoodie.” I think Price kind of didn't care if he died after Angela died.
Em: I think he didn't care if he died but he wanted to get Whiterose first. Once he handed off the drive (which he did right before going to the meeting), he had accepted his fate.
Freddy: You can't control people who have nothing to lose.
Em: Or to gain.
Micah: I like how Mr. Robot explained why he was there in the hotel room, instead of Elliot, by saying, "Life throws you an error code like that, you don't have the luxury of a fucking pop-up explanation."
The Bank Heist
Yael: Okay, so let’s talk about the hack. They said they needed to correlate phone numbers with bank account numbers to initiate the money transfers.
Em: They needed that for the script so they'd know which 2FA code to use for which request. Otherwise they'd have to brute-force it for each account, and that'd likely trigger a safety measure.
Micah: So Elliot and Darlene seem to have a SQL database from the bank, and their database includes account numbers, first name, last name, and hashed phone numbers. They needed to use the IMSI catcher (and the cell phone tower hack) to learn everyone's phone numbers, so they could hash them and then lookup the hashes in the bank database until they had phone numbers for all 100 accounts
Em: That's pretty realistic, FWIW. An equivalent of that was one of the first things we pulled from Phineas Fisher’s hack of Cayman National Bank and Trust (much to the dismay of some of the account holders).
Trammell: There was a CCC talk about nation-states doing 2FA intercept on Telegram password resets.
Micah: So, the venue changed. They got a hotel room within line of sight of the first venue, and they expected all Deus Group members to show up there, but the location moved. Mr. Robot figured out that Whiterose was at the first venue, though. So Darlene went to the second venue with the IMSI catcher, and Mr. Robot/Elliot stayed at the first venue to try to focus on just Whiterose's phone number. So all that hacking that Mr. Robot was doing, he was hacking into the telecom company that owns the closest cell phone tower.
Yael: How did Whiterose figure out that they needed a venue change and he had to get at Price?
Freddy: She said that Elliot disappeared right after Price said he was retiring, and that Price asked for a Deus Group meeting on Xmas, which was suspicious.
Micah: Elliot had a dump of Tyrell Wellick's phone, and it looks like he and Darlene imported Tyrell's Firefox passwords into Iceweasel, and then looked through his Google calendar. There was a password-protected attachment in one calendar event, and the thing I don't quite understand is how they got the password. I think Darlene sent it to him in Signal Desktop, but I don't know how they knew what it was.
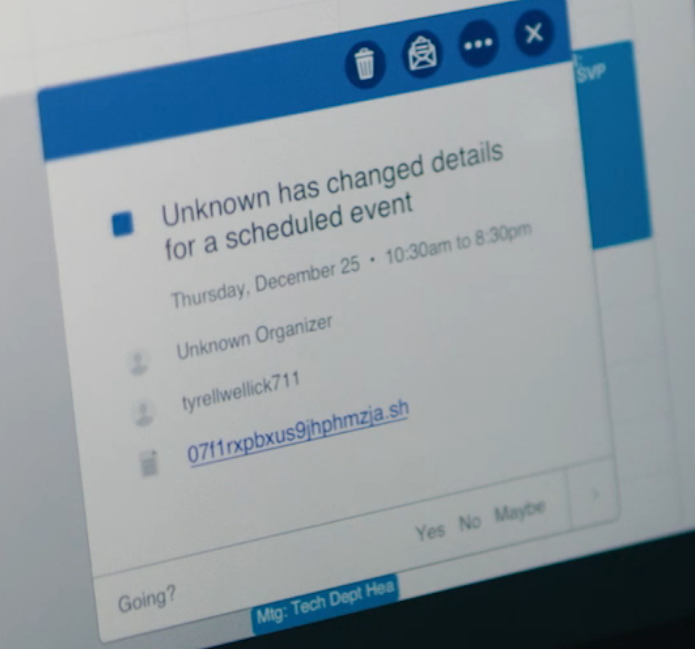
Freddy: It almost looked like a script to execute, but I couldn't tell. Maybe it was a pop-up?
Yael: I think it directed to a password-protected webpage hosted on some kind of private server. So I guess Whiterose got sloppy and forgot to take Tyrell off the list of people getting the venue change.
Micah: Tyrell was the guest of honor; he was getting named new CEO of Evil Corp. She just didn't realize he was dead.
Yael: I'm sort of stunned Whiterose didn't know Tyrell was dead or at least missing, with their surveillance..
Em: It happened in the middle of nowhere and the FBI didn't handle the crime scene, so the search around the van etc. was limited.
Yael: Yeah, but they had eyes on Tyrell and would've noticed he was missing after.
Hacking The Cell Tower
Micah: Okay, so let's talk about the cell phone tower hack.
Yael: Elliot was phishing telecom employees to try to get access to the cell phone tower because he didn't have the cell-site simulator.
Micah: Yeah, exactly. He needed to hack the cell phone tower, because that would give him the same access as if he had his own IMSI catcher. Once he got credentials from his phishing, he was trying to re-use them to login to the telco's VPN.
Yael: So what's easier and more reliable, building your own IMSI catcher or phishing telcos?
Freddy: Probably the latter, to be quite honest.
Micah: Also, did you notice that when he was phishing the telco, he scraped PGP keyservers to get a list of their email addresses? That's not realistic, though. Nobody in real life uses PGP. Except for The Intercept, but it's painful. I'm not sure all these gallatintelco.com employees would have keys on the keyservers.
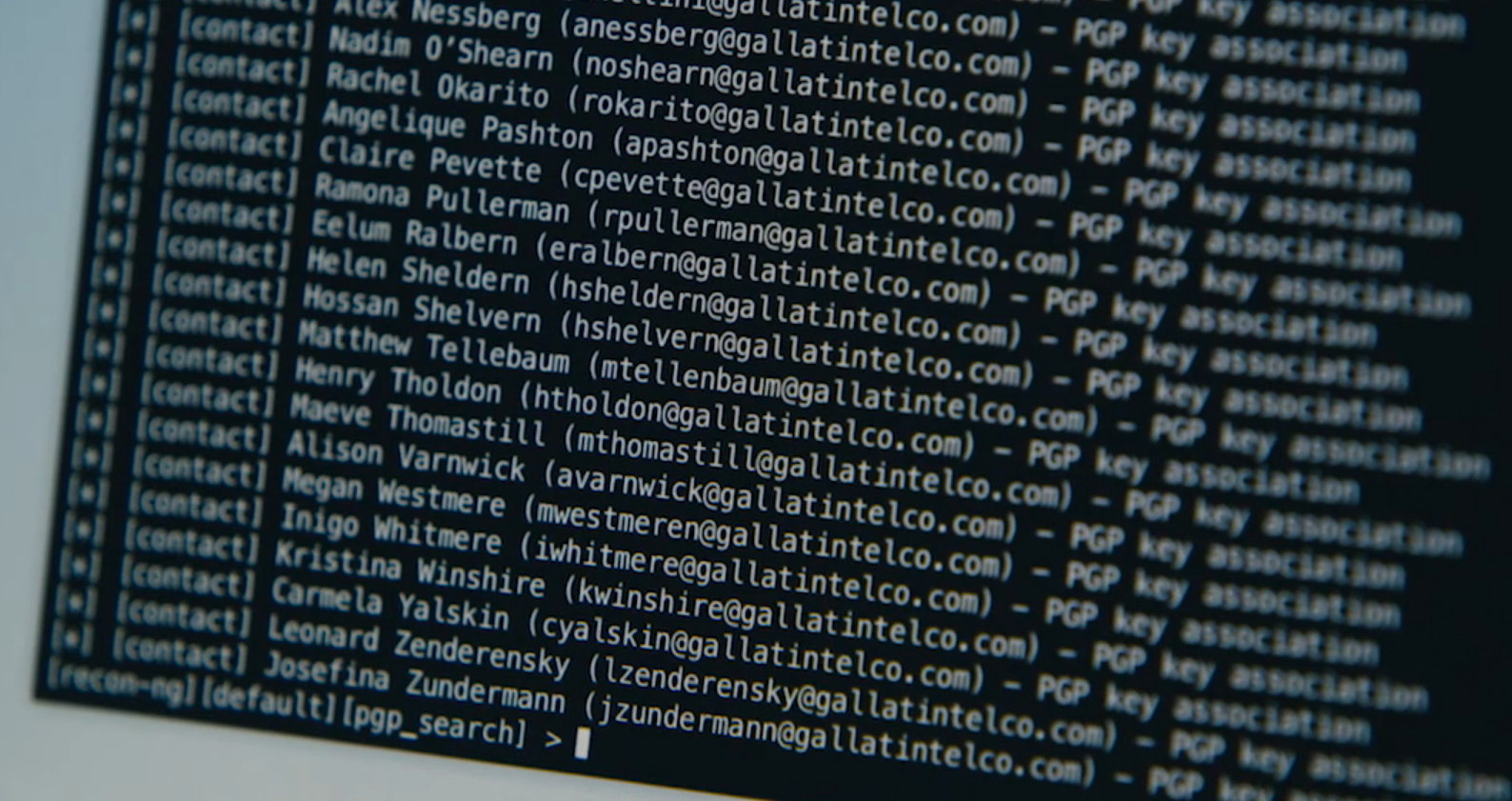
Em: It would only take one person uploading their set of public keys to get them there. Keyservers verifying permission of the owner to list the keys is relatively new, as far as I can tell.
Yael: Why does he need their public keys, though? How does this work?
Em: He didn't need the keys, he just needed the email addresses associated with them so he could phish the telco employees. He was basically IDing which email addresses were being used—rather than trying to get a list of employees and then figuring out the company’s email address format (e.g. jane.doe@gallatintelco.com).
Trammell: And he was hoping that one of them used the same password on the cell site infrastructure that they used to login in response to the phishing email. The first few didn't, but eventually one of them did. Someone always does...
Micah: It looks like USA Network didn't actually generate all these PGP keys. They're not in the SKS pool.
Trammell: Elliot’s ECorp key from the 2017 season is on the key servers. Or someone like me ran a key generator to spoof the 32-bit key id and uploaded it to the server and then registered e-corp.co.uk to complete the fake. 32-bit PGP key IDs are short enough that you can find a key that matches .
Freddy: I don't know any company, much less a telco, that requires you to publish PGP keys online.
Micah: The Intercept.
Yael: I think also the Electronic Frontier Foundation.
Freddy: When I used to work in cybersecurity I think I was the only one with a PGP key.
Micah: I think it's much more likely that a telco wouldn't be using any email encryption. But if they did, they'd use S/MIME, which is like PGP but centrally managed and therefore popular in the corporate/government world, and simpler to use.
Yael: I feel like I got PGP for street cred to get hackers I wanted to interview to talk to me vs. actually using it.
Micah: I used PGP to help facilitate the Snowden leak. Good times.
Garage Door Hack
Yael: Let’s talk about the garage door hack.
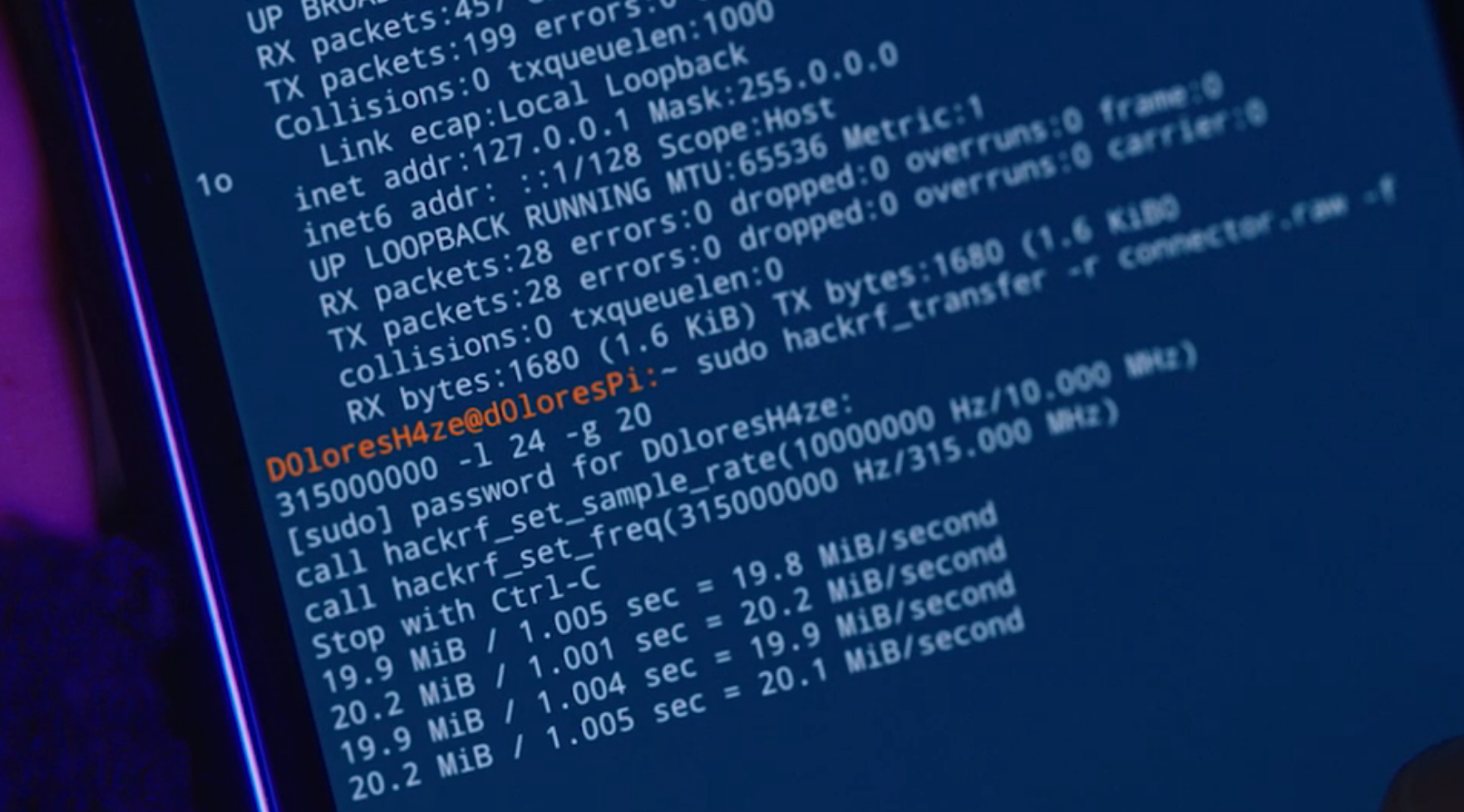
Trammell: Based on the scripts I think Darlene was using a HackRF. In that screenshot you can see that she has logged into a Pi with the HackRF and captured the signal while the security goon was pressing "close."
Bank Transfer
Micah: So as far as the bank transfer goes, I think there are some pieces of the puzzle that aren't quite clear in this episode. Last episode there was a snippet of python that involved mixing cryptocurrency. So I think they must have done something like this. Once they could spy on everyone's SMS, they initiated bank transfers for everyone, to transfer their money into some other bank account. When all the Deus Group members got SMS messages, they intercepted the 2FA codes and sent them to the bank to complete the transfers.
Freddy: Yeah but even then, you can't just do a bulk transfer of billions of dollars into cryptocurrency?
Micah: On the other end, the receiving account must have automatically been hooked into a cryptocurrency exchange, immediately selling all of that money for cryptocurrency, and then, immediately mixing that cryptocurrency.
Freddy: And do what with it? Someone will notice a trillion dollars being dumped into BTC (cough cough TETHER). Also, there is a cost to buying that cryptocurrency and you couldn't get the network throughput for syncing the transfers. Syncing a blockchain is much slower compared to something like SWIFT.
Em: Cryptocurrency for this is not realistic.
Micah: Before it could get exchanged for cryptocurrency, they had to have done a SWIFT transfer to a different bank. That must have been the first step.
Freddy: I am just saying, where did the money go? The cryptocurrency stuff is like "fancy Hollywood magic."
Micah: So maybe the money is all just sitting in like, a Swiss bank account or something that they set up just for this hack, and they're slowly working on moving it into cryptocurrency
Em: It would have to be several SWIFT transfers or things would not be accepted on the other end. Moving it all into one account wouldn't help, because it would be seized and returned.
Micah: It's a separate SWIFT transfer account for each Deus Group member, but still.
Freddy: Moving that much money would have tripped all sorts of liquidity rules at the banks.
Em: Yes, and the receiving accounts would have had issues with it. Even if all translated to BTC etc., they'd have to distribute it very widely to prevent it from being returned. A well set-up bank would also have additional confirmations required for transfers that empty out accounts or are over a certain amount.
Trammell: The liquidity of any of the cryptocurrency exchanges wouldn't be able to handle any significant buy-in like that. It would be like the flash crash in reverse.
Yael: Wait, I thought BTC couldn't get returned.
Em: Anything can be seized.
Micah: Yeah, I think once they get successfully get it into BTC, the only way they could seize it is by seizing the actual wallet, e.g. the secret keys.
Em: The exchange(s) are a vulnerable point, I think. Cryptocurrency would be harder to seize than a traditional account, if no one ever did anything with it. It'd have to sit there, dead.
Micah: If Elliot and Darlene can maintain their anonymity from the financial fraud investigators, they won't have any way of knowing who to seize it from. Also, if they don't actually want the money, they can just destroy the wallet.
Trammell: If they are doing the "K Foundation" attack rather than a "Robin Hood" approach, they could also transfer the BTC to a random address (or a symbolic one) where there is no secret key.
Em: There is one thing we're overlooking in the discussion of cryptocurrency transfers:
eCoin. We don't know how eCoin worked, but it's likely that it was more integrated with Cyprus Nat'l Bank than BTC et al is with most traditional banks.
Trammell: Good point—we're hypothesizing about how eCoin might work, as compared to real cryptocurrencies. (If eCoin is even anything other than a fiat currency issues by Evil Corp).
Em: I would be amazed if the bank wasn't integrated with it. And remember, eCoin wallets aren't secure against Evil Corp. They had the ability to look in every wallet etc.
Freddy: Presumably they also stole all the money from Price/Tyrell, too. So what's to stop them from bankrupting Evil Corp?
Trammell: I'm surprised that such rich people would have only one bank account. Their funds only have FDIC insurance up to $250k.
Em: What does FDIC insurance matter when the accounts are owned by the people who own the government(s)?
Freddy: Or for off-shore bank accounts.
Trammell: A more realistic response from Whiterose would be "oh, there's more where that came from."
Em: I think that's besides the point, considering the power dynamics at play.
Trammell: Offshore, different banks, different countries, etc. Single points of failure are so very dangerous.
Em: Whiterose would have been totally humiliated, all her data and everyone else's gone, their money taken—why would they give her more? The goal wasn't to bankrupt the members of the Deus Group but to bankrupt the Deus Group. Fsociety made Whiterose and the Dark Army bleed in a way that made them no longer appear invulnerable. Who would want to work with them then? But even arguendo, Whiterose would know the funds were gone for the immediate future and that'd ruin the Congo plan.
Darlene
Micah: I like that in the video Darlene told everyone the address of the Deus Group meeting, so that protestors showed up and stalled them from leaving long enough to complete the hack
Yael: haha yeah that was a fun distraction
Trammell: F L A S H M O B
Freddy: The only thing that rich people understand is an unruly mob.
Micah: Did you also notice the billboard for the fictional NBC TV show about fsociety called SHIFT+CONTROL?

Yael: Good name!
Micah: And the very last scene: Whiterose is putting on makeup while it appears a SWAT team is raiding her mansion and there's firefight going on? I think Whiterose is done.
Em: It's hard to tell. Zhang is done, definitely. Whiterose might not be. Though probably, given how close we are to the end of the series.
Yael: I was surprised when Price got shot. I knew he was gonna die, but didn’t expect it like that.
Em: He did such a good job of provoking Whiterose. It was beautiful.
Yael: That was a great episode. I was glad the hack finally happened and also that Darlene had a pivotal role in it. For Dom.
from VICE https://ift.tt/2RbBPAU
via cheap web hosting
No comments:
Post a Comment