Cops and spies all over the world are in the market for expensive tools that let them hack into phones and track down criminals. You’d think that none of them would want to purchase them from a guy described by competitors, former business partners, and researchers, as a "criminal of the worst kind" and “walking scam” with “shitty” products.
This infamous broker of spyware is still selling his wares, and he’s getting caught once again, according to a new report by security firm Cisco Talos.
The report, written by Cisco Talos researchers Warren Mercer, Paul Rascagneres, and Vitor Ventura, calls the company run by Manish Kumar an “infamous organization” with “a surprising level of amateur actions,” and “copy/paste” products.
Kumar’s Android malware, which the researchers dubbed WolfRAT, is based on DenDroid, a malicious software that was discovered in 2014, according to the report. DenDroid’s code was leaked online in 2015, effectively making it open source. The servers the malware connects to have been publicly linked to Kumar's company for more than a year, after researchers from another security company published a report about Wolf Intelligence, Kumar's company that sold surveillance and hacking tools to police and intelligence agencies.
Moreover, WolfRAT’s interface—the one that the hacking operators would use—looks exactly the same as the interface of Kumar’s previous products, according to the report, as well as an independent source who has direct knowledge of Kumar’s offerings. This source asked to remain anonymous to discuss sensitive issues.
“The malware itself is a poorly written and cobbled together using copy+pasted open source resources. Altogether it forms a mess of unused code and unused functionality,” Warren Mercer, the lead author on the report, told Motherboard. “We were able to link the campaigns off the previous research, from CSIS, which allowed us to overlap the command and control infrastructure that was being used by WolfRAT, including domains, almost identical C2 panel designs and largely re-used code across previous samples...oh and the fact that "Wolf Intelligence" was left in one of their C2 panels is interesting.”
Do you work or used to work at Wolf Intelligence, Coralco Tech or LokD? Or have you had any business dealings with Manish Kumar? We’d love to hear from you. You can contact Lorenzo Franceschi-Bicchierai securely on Signal at +1 917 257 1382, OTR chat at lorenzofb@jabber.ccc.de, or email lorenzofb@vice.com
The Android malware targets users in Thailand, and specifically messaging apps like Line, WhatsApp, and Facebook Messenger. The malware’s code is filled with comments in Thai language, the command and control servers are located in Thailand, and the server’s names contain references to Thai food, according to the report.
Cisco Talos researchers believe that after being exposed in 2018, Manish Kumar shut down Wolf Intelligence and now runs two companies, called Coralco Tech, which advertises itself as surveillance company and LokD, which purports to be a secure phone maker. The two companies did not respond to a request for comment.
Talos security researchers found a command and control server used by the malware that contained two user interface panels, one titled Coralco Archimedes, one titled Wolf Intelligence.
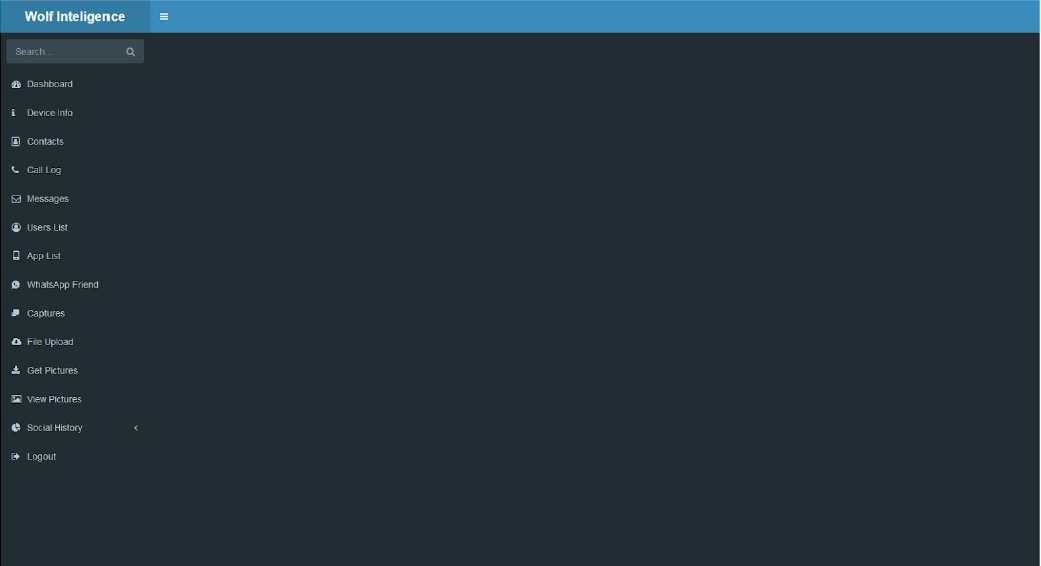
A source with direct knowledge of Kumar’s business, who asked to remain anonymous to discuss sensitive issues, said this is the same interface he saw years ago, when Kumar was running Wolf Intelligence.
In 2015, Kumar sent an Italian body guard to Mauritania to help close a deal. When the deal went wrong, the local government arrested the bodyguard, who was detained in the country for almost two years.. In 2018, security researchers from threat intelligence company CSIS found unprotected servers that contained data collected from targets hacked by Wolf Intelligence’s customers, as well as internal documents including a picture of Kumar himself.
“The absurd thing is that Kumar keeps selling this stuff,” said the source with knowledge of Kumar’s business. “I wish I knew who buys.”
Subscribe to our new cybersecurity podcast, CYBER.
from VICE https://ift.tt/3cMMHgG
via cheap web hosting
No comments:
Post a Comment