On Wednesday, a wave of high profile accounts including those of Joe Biden, Uber, and Apple tweeted cryptocurrency scams in an apparent hack.
Two sources close to or inside the underground hacking community provided Motherboard with screenshots of an internal panel they claim is used by Twitter workers to interact with user accounts. One source said the Twitter panel was also used to change ownership of some so-called OG accounts—accounts that have a handle consisting of only one or two characters—as well as facilitating the tweeting of the cryptocurrency scams from the high profile accounts.
Twitter has been deleting some screenshots of the panel and has suspended users who have tweeted them, claiming that the tweets violate its rules.
Do you know anything else about these account hijackings, or insider data abuse at other companies? We'd love to hear from you. Using a non-work phone or computer, you can contact Joseph Cox securely on Signal on +44 20 8133 5190, Wickr on josephcox, OTR chat on jfcox@jabber.ccc.de, or email joseph.cox@vice.com.
The panel is a stark example of the issue of insider data access at tech companies. Whereas in other cases hackers have bribed workers to leverage tools over individual users, in this case the access has led to takeovers of some of the biggest accounts on the social media platform and tweeted bitcoin related scams in an effort to generate income.
The screenshots show details about the target user's account, such as whether it has been suspended, is permanently suspended, or has protected status.
One of the screenshots is a Twitter user posting images of the panel themselves. At the time of writing that account has been suspended.
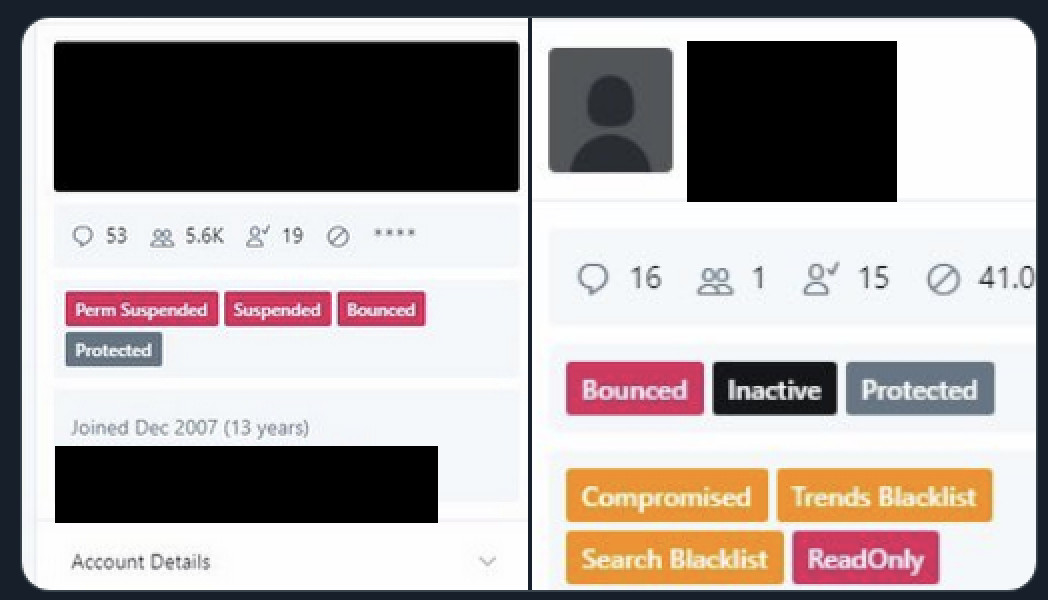
Data breach monitoring and prevention service Under The Breach obtained a similar screenshot and tweeted it as the worker hijacked several accounts. The person in control of the Under The Breach account told Motherboard Twitter then removed the tweet with the screenshot and suspended them for 12 hours. A message replacing the tweet now says it violated the Twitter rules.
It is not clear whether a Twitter worker carried out the compromises themselves with their access, or whether external parties gained access to the panel themselves.
A Twitter spokesperson told Motherboard in an email that, "As per our rules, we're taking action on any private, personal information shared in Tweets."
Other hijacked accounts include Mike Bloomberg, and cryptocurrency platforms Coinbase, Gemini, and Binance. The accounts falsely announced they had partnered up with an organization called CryptoForHealth which claims it was going to provide people with bitcoin as long as they sent some to an address first.
Shortly after the spike of takeovers, Twitter itself tweeted that users may be unable to reset their passwords or tweet while the company addresses the issue.
Within an hour of the breach, Republican Sen. Josh Hawley wrote a letter to Twitter CEO Jack Dorsey asking for more information about the hack, including how the hack occurred, how many users were compromised, and whether the hack affected President Trump's account. Hawley said "please reach out immediately to the Department of Justice and the Federal Bureau of Investigation and take any necessary measures to secure the site before this breach expands."
In 2017, a Twitter worker briefly deleted President Donald Trump's account before it was quickly reinstated.
Two former Twitter employees previously abused their access to spy on users for the Saudi regime, according to the Justice Department.
All tech companies face the issue of malicious insiders. Motherboard has previously revealed how Facebook employees used their privilege access to user data to stalk women; how Snapchat workers had a tool called Snaplion that provides information on users; and how MySpace employees abused a tool called "Overlord" to spy on users during the site's hayday.
Update: This piece has been updated to include a response from Twitter.
Subscribe to our cybersecurity podcast, CYBER.
from VICE https://ift.tt/2Zw7D7b
via cheap web hosting
No comments:
Post a Comment